iPhone vulnerabilities showed a new face when a Copenhagen based developer succeeded in developing integrity infringements that lead to automatic call connection. We have often seen links in webpages mainly while using mobile devices and they have phone numbers embedded in them. We can call these numbers by clicking on the link. But this vulnerability went beyond the norms and automatically connected to calls even if those are expensive ones.
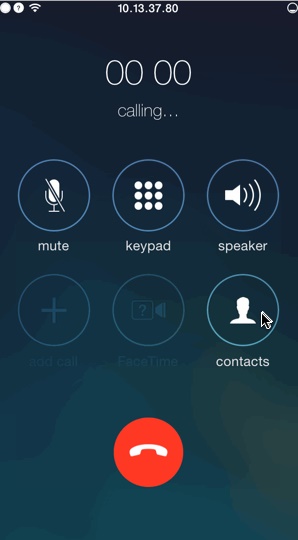
the name of the infamous developer is Andrei Neculaesei and he works with a wireless streaming company named Airtame. He made a simply way that broke the integrity of mobile apps like Facebook and Google+ and established call without the permission of the person being victimized. International calls that cost enormous were established at the cost of the users. When an iPhone user opens a webpage and taps on some phone number links using Safari web browser, he is asked for permission but the new technique created by Neculaessei bypassed the permission stage and calls got connected automatically which led the users in peril.
Neculaessei described the method and sent it via email
The person clearly mentioned the method that he implemented in abusing the security of iPhone users. He created a webpage that embedded a JavaScript. This Javascript caused a mobile application to trigger a call whenever a user opened the webpage. The Javascript overcame the conventional process and launched the Unique Resource Identifies (URI). The links could be transmitted through malicious links in Facebook or Messenger app. The threat also worked for apps like Apple’s Facetime, Google’s Gmail and Google + applications.
Check the whole process in Animation here.
Image & gif: Andrei Neculaesei






Leave a Reply